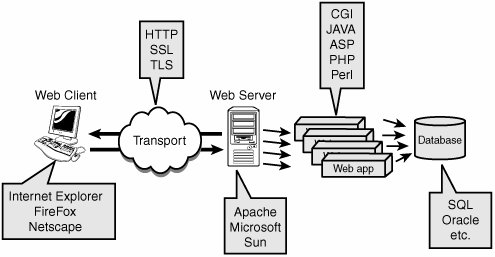
Hacking Web Servers.
Although there are several ways to hack a web server, the simplest method includes using something called SQL Injection, which involves running operating system commands on the web server. If you are familiar with how to do this, the next step would be to run commands like "flush cache" and "delete all files" to remove data that was kept on the server. Following that, you might want to visit other websites connected to the same network so they can view the removed data. A simple Port Scan is useful in this situation. A straightforward port scan is comparable to checking a house window at night to see whether somebody is inside. This kind of scan will display open ports and active services on a Windows server.
Web Server Hacking:
Once you know which ports are open, you can use additional operating system commands to learn more about the network, such as tracers and ping. If you want to take things a step further, you may connect to web servers on the network using the netcat software and record any data that is sent from them (like usernames and passwords). Given that you have immediate access to all of their internal network resources, this is a very potent strategy.
Finally, if you want to access networks covertly, you should always utilize a conversion channel. This entails sending data that is typically utilized for something else through a public protocol. For instance, consider IRC (Internet Relay Chat). Computer aficionados use it to discuss technology and other nerdy topics. It was actually developed more than 20 years ago as an alternate method of internet data transmission. The main benefit is that IRC runs by default on TCP port 6667 and doesn't require a username or password. They don't have time to figure out what you are doing by collecting your packets, making it a great approach to obtaining internal data from networks.

Steps to Hack:
reach out to the web server.
To access this network anonymously and scan ports for open ports, gather more information.
Pay attention to the system's file sizes, open ports, and active processes.
Connect to websites that are part of the same network as Twitter and Facebook so they can see what information was removed.
Access the server by means of a conversion channel.
To learn more, use the data and resources on the internal network.
To acquire remote access to these sites, use Metasploit (also see, Metasploit Ethical Hacking Edition e-book download).
Key Points:
An SQL Injection is a great technique for a beginner because it is quick and simple to use to hack a web server.
Similar to "hacking," accessing internal network resources using a public internet connection like IRC is quick and easy.
Through a conversion channel, SQL Injection can be used to obtain access to other networks on the same subnet.
This process is known as a "Simple Port Scan." This can assist you in learning more about potential network resources for subsequent exploitation.
Conclusion:
Updating the software is a good idea if you are managing your own web server. Keeping up with Java, PHP, and Python is part of this because they all have security problems. Additionally, ensure your operating system has been updated so it includes the most recent Microsoft updates. This can assist in preventing any inbound or outgoing vulnerabilities that a hacker might employ to access your web server or impair service. Finally, seek professional advice on how to set up real-time monitoring for any unforeseen activities after creating a new database on your web server.
What are keyloggers and how do they work?
It’s 1976. a Cold War. Monday morning sees the arrival at work of an American diplomat assigned to the American embassy in Moscow. He types his reports on his IBM Selectric typewriter while seated at his desk. He believes he is safe. He has no idea that every word he types is being captured.
The first keylogger in history, a miniature set of circuits squeezed into a metal bar that ran along the typewriter, was used by the Soviets to bug his typewriter. It could capture each keystroke and relay the information in real-time while remaining hidden from view. The Americans would learn of this after eight years.
What are keyloggers?
Keyloggers, also known as keystroke loggers, are programs or hardware devices that keep track of each keystroke you make on a computer or mobile device.
Keyloggers that are more sophisticated track everything from your copy-and-paste keyboard and GPS data to your camera and microphone recordings. Basic keyloggers log keystroke inputs performed on text files.
Back then, keyloggers were exclusively hardware-based. But because we live in a digital world, software keyloggers have become more common. Let's examine each in more detail.
Hardware keyloggers:
Keyloggers on hardware are much less frequent than keyloggers on software. After all, downloading a file or clicking a link is simpler than sneaking a USB stick into someone's laptop. Nevertheless, your device may occasionally come with hardware keyloggers that were either included by the manufacturer or a third-party company.
Even without being connected to your computer, a covert camera might be used to record your keystrokes. They may be positioned in public areas like cafes or libraries.

Software keyloggers:
The majority of keyloggers are software-based. Software keyloggers monitor keystrokes and record everything you type while running in the background.
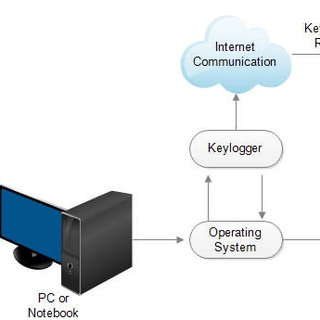
How do keyloggers work?
Keystrokes are your computer's language. Your computer receives a signal when you press a key telling it what to perform.
This exchange between you and your computer is often private. Keyloggers, on the other hand, behave like nosy neighbors who watch, listen in, and record each keystroke you make. They record which key is pushed, how quickly you press it, how long you press it for, and when you press it.
The keylogger then stores all of this information in a little file. While hardware keyloggers need the owner to physically extract the files, software keyloggers send the owner regular updates with the saved data.
Types of keyloggers:
Keyloggers have genuine, lawful purposes despite their espionage-related beginnings. However, not all states or nations need keylogger users to formally get permission from the subject of their surveillance.
We're categorizing keylogger usage into three groups for this reason: legal consensual use, lawful non-consensual use, and illegal use. Starting with the former,
How to detect keyloggers:
Since keyloggers are frequently undetectable, identification is challenging but not impossible. Here are a few red flags that a keylogger is present on your computer or phone:
It's taking longer than usual: Your device performance may deteriorate if you record and send every keystroke you make.
Your options have been modified: Is your computer automatically switching to a new browser that you didn't install? Or maybe a brand-new toolbar just appeared out of nowhere? These could indicate the presence of a keylogger on your computer.
Unexpected freezes or crashes: Similar to the first point, sending all that keylogging data may strain your system and result in app or system crashes.
However, only keyloggers with poor design exhibit these symptoms. Many keyloggers are very difficult to find. Keyloggers that are particularly persistent could hide inaccessibly deep inside the operating system of your device.
And things get increasingly trickier when it comes to hardware keyloggers. Your only possibility of finding the keylogger is if you physically disassemble your gadget. Only a trained technician should attempt this.
.png)
.png)

.png)
No comments:
Post a Comment